Work off campus
Work off campus¶
Virtual private network (VPN)¶
Some applications require a connection to École polytechnique's or IDCS partner laboratory's internal network. In these cases, a secure VPN connection is used. You'll find an exhaustive list below for the IT resources of IDCS partners laboratories.
You will need to install a VPN client on your workstation1; by installing this client you will of course undertake to apply the best practices laid down by the ANSSI in terms of mobility and nomadism on your hardware configuration, and authorize an SSI audit of your hardware configuration on simple request from the School's CISO.
The VPN solution will enable you, subject to the performance of your web connection, to access the resources of the School's IT resources or IDCS IT partner laboratory resources under the same conditions as if you were on site. It is available for :
-
administrative staff equipped with a workstation1 supplied, controlled and verified by the School's IT department or IDCS partner laboratory's IT department. If Palo Alto Global Protect software is not installed, you can get it here.
-
research staff2 equipped with a workstation1, controlled and verified by the School's IT department or IDCS partner laboratory's IT department. If Palo Alto Global Protect software is not installed, you can get it here.
requirements
The workstation must be checked by the IDCS laboratory's partner system administrator (ASR) or security correspondent (CSSI). Using VPN on a personal computer is prohibited.
Connect it¶
To connect, on MacOS, click in the top right-hand corner on the icon  .
.
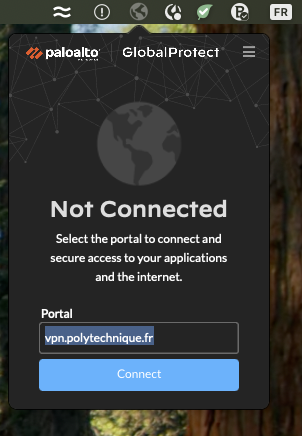
The vpn.polytechnique.fr portal only needs to be entered once after installation.
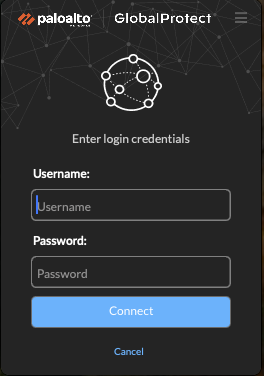
Enter your School's login and password (eg. firstname.lastname) :
Application lists¶
| Name | IDCS Laboratory Partner | Description |
|---|---|---|
| Lina | CMLS-CPHT-CMAP-OMEGA | Backup for workstation and laptop |
| GLPI | CMLS-CPHT | Hardware and software inventory |
| Cholesky | ALL | Cholesky HPC cluster |
| GITLAB IDCS | ALL | Cholesky HPC cluster projects management |
| File servers | CMLS-CPHT-CMAP-OMEGA-CRG | Drives or data storage facilities |
| Printers | ALL | School's papercut printers |
SSH remote access¶
Each IDCS partner laboratory provides SSH remote access to their laboratory IT resources or IDCS IT resources by a SSH input gateway.
graph LR
You --> SSH-Laboratory-Gateway
SSH-Laboratory-Gateway --> ServerX
SSH laboratory input gateway¶
ssh.cmls.polytechnique.fr
ssh.cpht.polytechnique.fr or pascal.cpht.polytechnique.fr
SSH remote login is only allowed with SSH Key pair.
SSH Key generation¶
-
Linux or MAC OS X
-
In a terminal, check on your computer that you don't have a key pair :
$ cd ~/.ssh $ ls authorized_keys2 id_rsa known_hosts config id_rsa.pubFind a key pair like
id_rsaandid_rsa.pub(orid_ed25519andid_ed25519.pub). Thepubfile is the public key (which can be communicated to anyone) while the other is the private key. If you don't see these files, it is necessary to generate them.RSA Algorithm
It depends on the size of the key. A key length less than 4096 bits is now considered not secure. So, we recommend to use the
ed2556algorithm from now on.Ed25519 Algorithm
It’s the most recommended public-key algorithm available today. The Ed25519 public-key is compact. It only contains 68 characters, compared to RSA 3072 that has 544 characters.
-
In a terminal, run this command
ssh-keygenwithed25519algorithm:$ ssh-keygen -t ed25519 -
This command asks you to save the key in the default file
id_ed25519file, then asks a passphrase to protect the private key :Generating public/private ed25519 key pair. Enter file in which to save the key (/home/ubuntu/.ssh/id_ed25519): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/ubuntu/.ssh/id_ed25519 Your public key has been saved in /home/ubuntu/.ssh/id_ed25519.pub -
Transmit the public key
id_ed25519.pubto IDCS IT support. -
IT support will then copy the contents of your public key into
~/.ssh/authorized_keysof yourhomedirectory and then confirm you that you can connect to the gateway.
-
-
Windows (with PuTTY)
-
Download and install SSH client : PuTTY
-
Run the tool
PuTTYgenet selectED25519as the key type, then click onGenerate: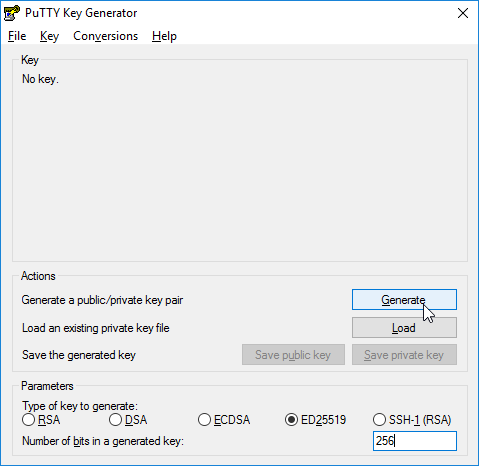
-
Move your mouse cursor randomly in the area below the progress bar, as shown below :
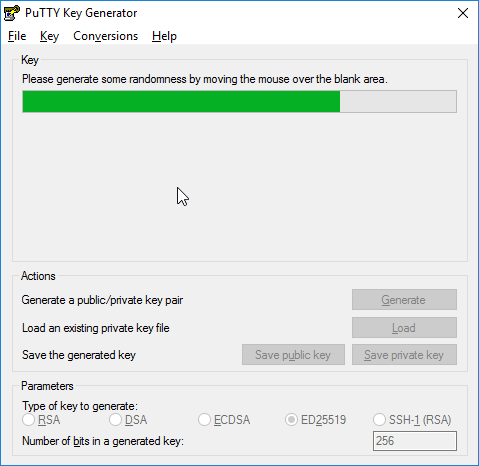
-
Once the progress bar is complete, the window below appears and asks you for a key passphrase that protects the private key :
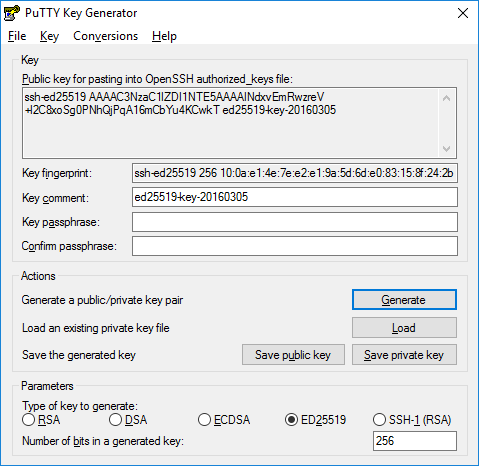
-
Transmit the public key in the field starting with ssh-ed25519... to IDCS IT support.
-
IT support will then copy the contents of your public key into
~/.ssh/authorized_keysof yourhomedirectory and then confirm you that you can connect to the gateway.
-
SSH client configuration¶
With SSH you could create the file $HOME/.ssh/config to simplify some ssh setup, like:
- fix some options.
- fix remote username for one host.
- use host alias.
Host aliases¶
The following example of config file, defines two aliases: cpht and cholesky. They make the command line shorter to connect you to the cholesky frontend. Thus, ssh <your_login>@cpht.polytechnique.fr is replaced by ssh cpht. Note that the alias cholesky reuses the alias cpht so as to bounce on the SSH CPHT gateway before connecting to the cholesky front head (if you have registred cpht as your connection machine).
Note
Replace <your_login>, and <path_to_ssh_key> with your own setup.
Host *
ForwardAgent yes
Host cpht
HostName ssh.cpht.polytechnique.fr
User <your_login> # replace with your own login
ForwardX11 yes
IdentityFile <path_to_ssh_key> # replace with your own path, e.g. ~/.ssh/id_rsa
Port 22
Host cholesky
HostName cholesky-login.mesocentre.idcs.polytechnique.fr
User <your_login> # replace with your own login
IdentityFile <path_to_ssh_key> # replace with your own path, e.g. ~/.ssh/id_rsa
Port 22
ProxyJump cpht # proxy jumping with cpht
-
laptop or desktop computer prepared and provided by an IDCS partner laboratory's IT department, also known as a "trusted terminal". ↩↩↩
-
permanent researcher, scientific collaborator3, PhD, post-doc, trainee, student. ↩
-
for scientific collaborators from outside the IDCS partner laboratory, a certificate of computer security compliance will be requested from the collaborator's home laboratory. ↩